In the former issues of Technical Insights, data recovery experts from the Key Laboratory of Sichuan Province(Subsidiary of SalvationDATA) explained their researches on extraction of cellphone audio files, the recovery of SQLite database files, the writing of forensic scripts for cellphone apps, and the mining of data through defensive cellphone apps etc. The focus of this issue is the various means of data extraction from iPhones (either jail-broken or not) that can give access to all types of data, including texts, images, audios and videos.
With the continuous development of mobile communication technology, cellphones has become an indispensable tool for interpersonal communication and almost everyone carries one or more cellphones. A great deal of information recorded by cellphone apps, chats and locations for example, would probably become the key for investigators to crack cases. Cellphone data extraction, therefore, bares great importance.
To provide support for data extraction from Android phones is the priority for data recovery experts since Android phones are still the leader in the cellphone industry. Data issued by ZDC (Zhongguancun Internet Consumption Research Center) indicates that in 2015, Samsung ranked the top in terms of cellphone brand awareness, as shown below in Picture 1. Apple, following Huawei, merits attention as the third place and indicates the importance of support for iPhone data extraction. Means of data extraction from iPhones are discussed in ensuing paragraphs.
Same as Android phones, data extraction from iPhones also falls into two categories: those that are jail-broken and those are not.
I Data Extraction from Non-jail-broken iPhones
Data extraction from non-jail-broken iPhones is mainly done through data back-up and sandbox extraction. Due to the fact that iOS systems above 8.3 no longer support sandbox extraction and that it can be done easily, sandbox extraction is not covered here in this issue. The following introduces how to extract data through data backup.
- Data Backup
Data backup can be accomplished via two approaches:
(1) Backup through iTunes. Back up path for XP systems: C:\Documents and Settings\User Name\Application Data\Apple Computer\MobileSync\Backup;
For WIN7 systems and above: C:\Users\User Name\AppData\Roaming\Apple Computer\MobileSync\Backup.
(2) AppleMobileBackup.exe Command. For example: AppleMobileBackup.exe -b –target befd8222746f2d52b9f2f40e862444208b3d423f ( ID for the target device can be viewed in itools) -q “c:\temp\2016-05-18-15-37-42”.
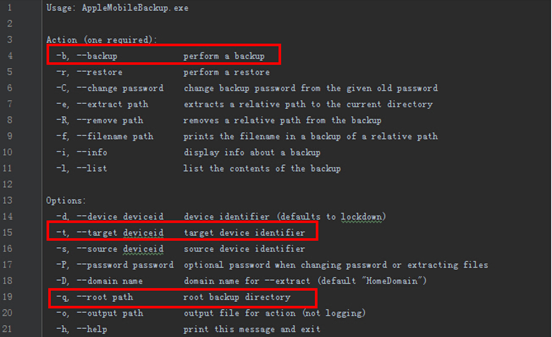
Picture 1 AppleMobileBackup.exe Command
Shown in Picture 2 are all the commands, among which three, -b (backup), -t (target device ID) and -q (root path) (framed by red boxes in the above picture) are used and introduced here.
- Data Analysis
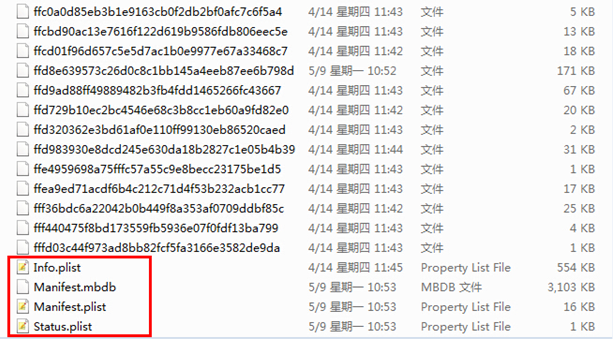
Picture 2 Backup Catalog (In the red box are plaintext files)
Under the backup catalog are a great pile of files that are named as 40-digit hexadecimal numbers, as shown in Picture 2 and these are data files of different apps. How could one find required data from all these files? Useful information could be found in the plaintext files that are shown in the bottom of the picture.
(1) Info.plist
This file in plist format can be opened by a plist editor and has information on users, devices, and backups (picture 3).
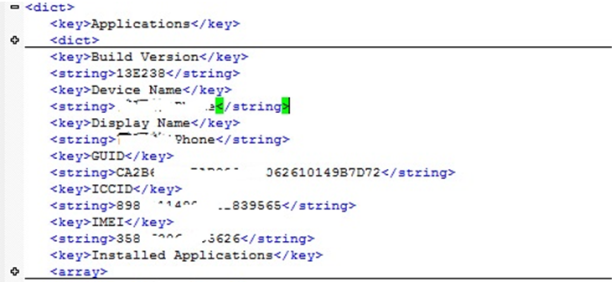
Picture 3 :Info.plist File Content
(2) Manifest.plist
This file contains information on installed applications and users, including application package names, version numbers, and installation paths etc.
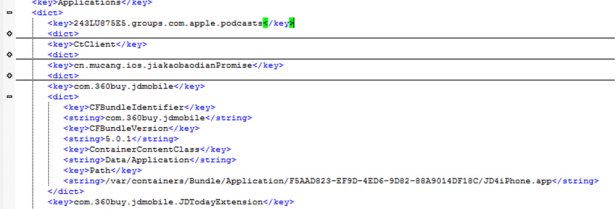
Picture 4:Manifest.plist File Content
(3) Status.plist
This file covers information on backup state, backup date and time, whether it is a full backup, backup UUID and others. Shown in picture 5.
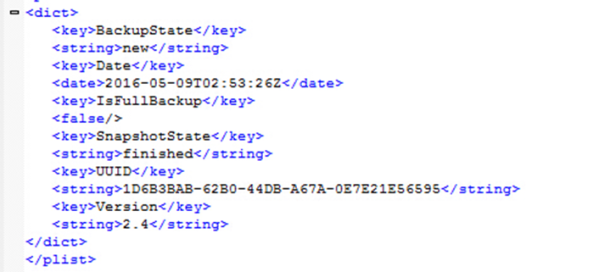
Picture 5:Status.plist File Content
(4) Manifest.mbdb
This is the most important and most complex file that documents all backup information. Correspondence between files and applications and file path can be found in this file.
Before continuing the presentation of this file, an introduction to ‘Domain Name’ must be covered. A domain name is used to locate files through its full path in the cellphone, for example AppDomain-com.meitu.myxj represents path /var/mobile/Applications/.
Access to domain names and paths could be reached by opening the file using NotePad++ (Picture 6).
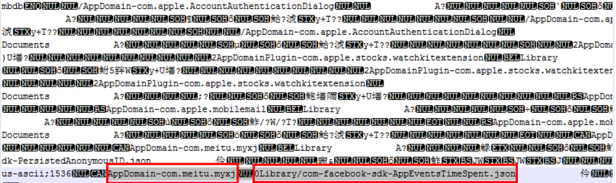
Picture 6:Manifest.mbdb File Content
From the red-boxed line in the file (Picture 6), one can get the domain name* and file path**. Using SHA1, one pair of basic information (domain name plus file path) can be encrypted into a 40-digit hexadecimal number that matches one of the file manes listing above. The correspondence between a file and its path could be obtained in this means.
* (AppDomain-com.meitu.myxj)
** (Library/com-facebook-sdk-AppEventsTimeSpent.json).
For example:
The encrypted number got from SHA 1 for AppDomain-com.meitu.myxj-Library/com-facebook-sdk-AppEventsTimeSpent.json is 5ee0c32e727e1a89605ee018aa9b6fd173001b57, also the file name of this path.
The above-mentioned way is too time-consuming and effort-demanding if one needs to backup all files. But after knowing the file structure, texts can be parsed by codes to reduce labor costs. File structure of Manifest.mbdb is explained in the following paragraphs.
The hexadecimal structure of a file can be viewed through WinHex (Picture 7).
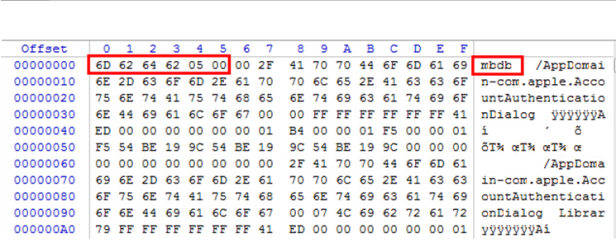
Picture 7:Hexadecimal Structure of Manifest.mbdb
A File Header
The red-boxed data in picture 8, the first 6 numbers, are the file header for the file.
| Type | Value |
| Uint8[6] | mbdb\05\00 |
B Contents
File contents are variable-sized records that document detailed information of the file.
| Type | Information | Note |
| string | Domain Name | Domain Name (first two numbers are name size and the rest are name value ) |
| string | File Path | File Path (first two numbers are data size and the rest are data value ) |
| string | Link Path | Absolute Path of Symbolic Link (first two numbers are data size, 0xff 0xff means no Link Path, and the followings are data value) |
| string | SHA1Abstract | Usually empty,
First two numbers (0xff 0xff) means a file in app domain, (0x00 0x14) means a file in system domain The following 20 digits forms a 40- digit hash value as the SHA 1 Abstract |
| string | Key | First two numbers as (0xff 0xff) means unsecured,
Otherwise means key length |
| Uint16 | Path Type | 0x4000- catalog (all beginning with 4 are catalogs)
0x8000- file (all beginning with 8 are files) 0xa000- symbolic link (all beginning with a are links) |
| Unit64 | Note Number | Search entry in note number |
| Unit32 | User ID | Usually as 0x000001f5 = 501 |
| Unit32 | Group ID | Usually as 0x000001f5 = 501 |
| Unit32 | Time of Last Modification | Time stamp accurate to the second |
| Unit32 | Time of Last Visit | Time stamp accurate to the second |
| Unit32 | Time of File Creation | Time stamp accurate to the second |
| Unit64 | File Size | 0 stands for links or catalogs |
| Unit8 | Protection Class | 0x001~0x0B |
| Unit8 | Number of File Attributes | Notes the number of file attributes of the following file,
Extraction of attributes are the same as domain names: Attribute Name: first two numbers are name size and the rest are attribute name Attribute Value: following attribute name, first two numbers are value size and the rest are attribute value |
All backup files can be decrypted using the above-mentioned file structure. If only a certain specified file needs to be parsed, knowing file path and its domain (such as for texts, domain name and file path are fixed) backup file can be found using SHA1 value and then extract data. If unknown files need to be parsed, with unfixed path or unknown domain name, data can be extracted only by decrypting Manifest.mbdb file.
II Data Extraction from Jail-broken iPhones
Jail-broken phones have the highest authority to the system and can access application data directly. The following are a few common-used catalogs:
- System Application Catalogs
①/private /var/ mobile/Media /DCIM/ Image Catalog
②/private/var/ mobile /Library/SMS/ Message Catalog
③/private /var/root/Media/EBooks/ EBooks Catalog
- User Application Catalogs
Data of applications installed by users are stored under
/private/var/mobile/Containers/Data/Application/.
Detailed explanation is made taking a financial application as an example.
Path for the APP is /private/var/mobile/Containers/Data/Application/3ADDACBE-7FDB-4726-AC47-4F1EFD0702B5/. The following means is used to figure out which application these data were from.
Open the catalog, a file named ‘.com.apple.mobile_container_manager.metadata.plist’ can be seen. The file name indicates that it is a management document and contents in Picture 8 can be viewed after opening the file.
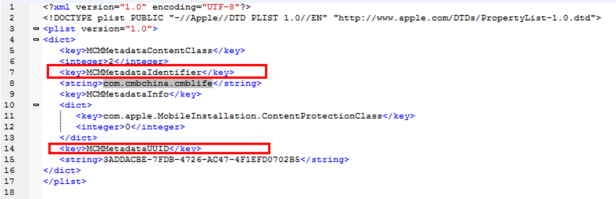
Picture 8:.com.apple.mobile_container_manager.metadata.plist File Content
Red-boxed in Picture 8, corresponding value of ‘MCMMetadataUUID’ is the hash value in the catalog, ‘MCMMetadataIdentifier’ the application package name. Knowing these information, one can extract data by parsing a specified application.
III Conclusion
Although data can be extracted from non-jail-broken iPhones by data backup, partial data are still inaccessible due to the lack of highest authority. Moreover, the process of backing up all files and then parsing required ones increases the time of data extraction. Jail-broken phones, having highest authority, can access files directly without going through data backup, which saves time for the data extraction process.
Some forensic equipment on the market is using these means to do data extraction; Track Visualization Forensics System in MTF cellphone from SalvationDATA is one of them. This system combines all these means and can extract and analyze data from phones (either jail-broken or not) faster to gain access for application information on chats, tracks, shopping, and accounts, and deleted behavioral information.
Click HERE to learn more about MTF.

Reblogged this on Người Đến Từ Bình Dương.
赞赞