When it comes to computer forensics, the capability to extract and analyse Mac log is very essential. Since Mac log file cannot be recognized on window system, its structure needs to be parsed so that we can proceed further analysis. In this issue, data recovery experts from the Key Laboratory of Sichuan Province introduce the structure of Mac log files, and how to use the SalvationDATA (DF)Digital Forensics System for its analysis and extraction.
I What is Mac log file?
Mac log files are files that record computer system applications and service activities with the suffix “.asl”, whose full name is Apple System Log. Mac log files are stored by day and are mainly divided into 7 major categories, i.e. system log, installer log, wireless connection log, VPN connection log, core log, diagnostic log and power management log, whose storage formats are all “.asl”. As the Mac log data is stored in binary, and the file can not be identified on Window system, the asl log file structure needs to be parsed so that we can proceed further analysis.
II Mac log file structure
1. Log header
The structure of Mac log file storage is asl, and it is found that the asl file consists of file header and log records. The file header length is fixed at 80 bytes. Its structure is shown in Picture 1.
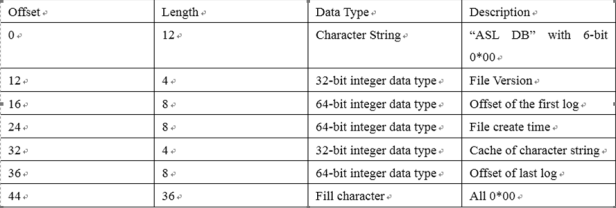
Picture1
The log header file records the location where the first log record is stored, and each record records the offset of the next one. Each log record length is non-fixed. The structures are shown in Picture 2.
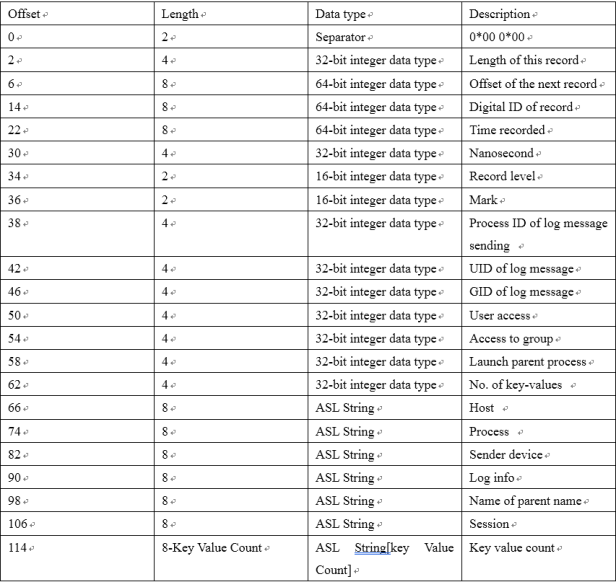 Picture 2
Picture 2
2. Log level
Mac log file is divided into eight levels from 0 to 7 with each number representing a different meaning, as shown in Fig. 3.
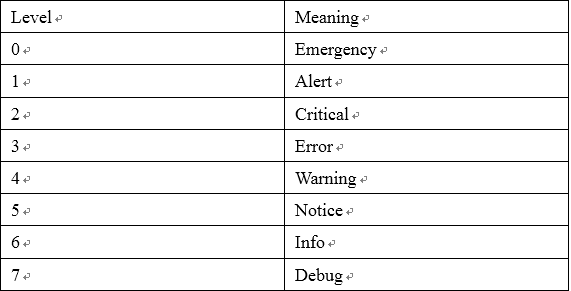
Fig.3
3. String Format of ASL STRING
ASL String is a special string storage format:
When the stored string is <= 7 bytes, the first byte is set as 1, the remaining 7 bytes store the string data. String whose length is less than 7 bytes is filled with 0x00;
When the stored string is > 7 bytes, the first byte is set as 0, and the entire 8 bytes are regarded as the real data offset, pointing to the stored string.
Example of String data length <= 7 bytes:

Picture 4
The binary with first byte of 0x86 is represented as: 10000110, the first is 1, that is, the following 7 bytes represent the stored string data, the encoding scheme is UTF-8, and the result is parsed to be “powered”, as shown in Picture 4.
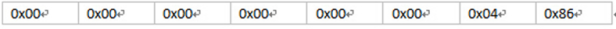
Picture 5
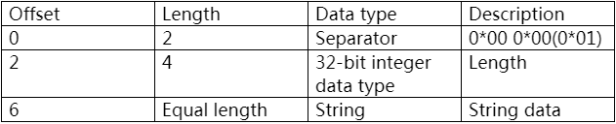
The binary of the first byte is represented as: 0000 0000, that is, the entire 8 bytes represent the offset of string in the entire log file. Winhex tool is used to jump to the corresponding data, as shown in Picture 6.
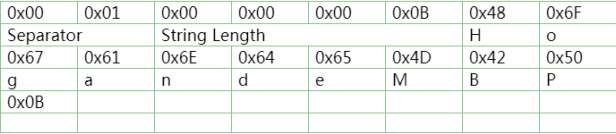
Picture 6
The string length is 0x0B, the encoding mode is UTF-8. The result is parsed to be HogandeMBP, as shown in Picture 7.
Picture 7
Note:
Time is unix timestamp (UTC), 1970-01-01 00:00:00 is used as the reference time; byte storage order is big endian storage.
III Parsing Mac log data with DF
1. Run SalvationDATA DF, add the Mac image file and load the Mac log file, as shown in Picture 8.
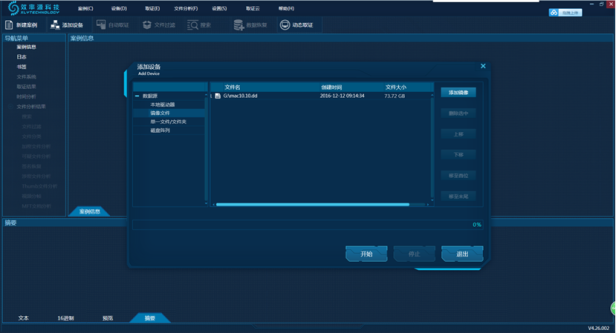
Picture 8
2. Click Auto Forensics, select Mac System Log and start extraction, as shown in Picture 9.
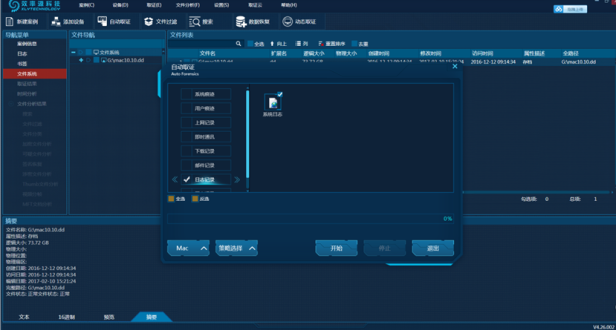
Picture 9
3. View the log parsing results, as shown in Picture 10.
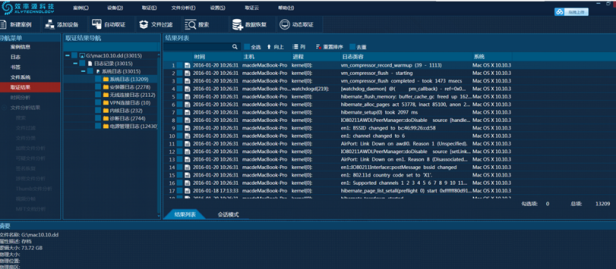
Picture 10
IV Conclusion
In this issue, data recovery experts from the Key Laboratory of Sichuan Province introduced the structure of the Mac log file, and how to use SalvationDATA DF(Digital Forensics System)for its analysis and extraction. Specifically designed for forensic analysis, DF has such functions as rapid forensics, data extraction, traces extraction, data analysis, report analysis etc..
Please stay tuned for more information about DF.
