Editor’s note: In this issue, experts from SalvationDATA will introduce several ways to reach surveillance host, which could help improve the efficiency of evidentiary data extraction during field investigation.
DVR forensics techniques, with its application being used more often in field investigation, is now being considered as the one of the four crucial techniques for case cracking. In fact, it’s so important that having a sound DVR forensics platform has been deemed as an indicator of the case handling capability of a police department and advancement of a nation’s criminal investigation techniques. That explains why a nation puts so much importance on deployment of proper DVR forensics system.

1. Overview
As one of the most important and practical function, Extraction via LAN, when coupled with functions like extraction, recovery, ultra-playing, video retrieval, image enhancement, map labeling and case management, form a powerful DVR forensics system that can help field investigators improve case cracking efficiency. And it is preferred by users for the following:
1.1 Removal of DVR Hard Disk Not Required
Video materials can be extracted directly via LAN, removal of DVR hard disk is not required.
1.2 Manager Advice Not Needed
Extraction via LAN abandons the old practice of asking site managers for surveillance host information or manually configuring IP address of surveillance host. With Extraction via LAN, the surveillance host information can be obtained without much manual operation.
1.3 Manual Input of IP Address Not Needed
VIP will automatically search surveillance host within the LAN when IP address is configured. Once the surveillance host is found, video material related to the case can be found easily.
You may find that some NVR/DVR software on the market are with the function of Extraction via LAN, but it requires investigators to manually configure IP address of surveillance host and COM port. And it’s possible that some of the IP addresses and COM ports may be omitted, and the number of NVR/DVR acquired is not accurate. To facilitate DVR forensics process demands a kind of DVR forensics software that can obtain surveillance host information automatically.

2. Solution
It is suggested by experts from SalvationDATA that the surveillance host information can be obtained automatically via the following 3 methods.
2.1 Protocol Detection
Protocol detection, as its name indicates, works through TCP or UDP protocol. A special data packet is broadcasted within the LAN first within the LAN via TCP/UDP, when it is received by surveillance host, some crucial information like brand name, model, IP address, COM port, type and channel of a surveillance host will be returned. No data or error will be returned if the DVR/NVR is not surveillance host. It’s pretty clear now which one is the surveillance host.
The whole process resembles roll calling, to figure out whether Xiao Ming is present or not can be as simple as calling his name.
The protocol of those renowned NVR/DVR brands is not open to the public, it may take some effort before they can be obtained. Investigators are suggested to use vendor test program and sniffer like WinPcap to get its protocol.
Take Hikvision as an example. With the surveillance host search function of Hikvision’s test program and the returned data packet by WinPcap, the protocol packet(not all) of Hikvision’s surveillance host is obtained(shown as below):
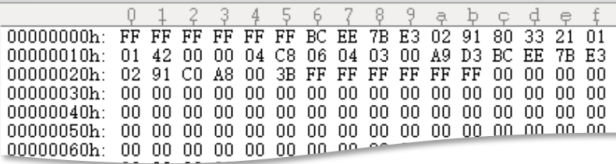
In it:
FFFFFFFFFFF is the Mac address of Receive Packet
BCEE7BE30291 is the Mac address of Sending Packet. And it is Mac address of Receive Packet when it is returned, therefore, it is indeed the Mac address of surveillance host.
Surveillance host information is obtained by simply broadcasting the data packet mentioned above.
The convenience Protocol Detection offers is that the detection process is automatic and fast. But analyzing protocol requires much effort.
2.2 SDK Search
When Protocol Detection is not possible, SDK Search is used as an alternative. SDK tools are provided by many developers nowadays for ease of secondary development. And surveillance host search function is embedded in the tools provided by some. These search functions can be used for detection of surveillance host.
Take Raysharp and Woshida as an example:
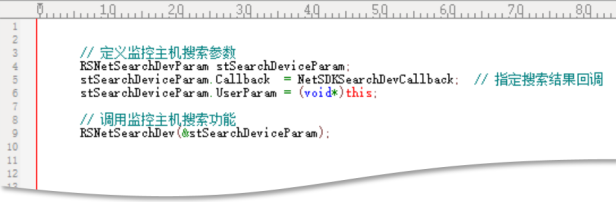
Raysharp
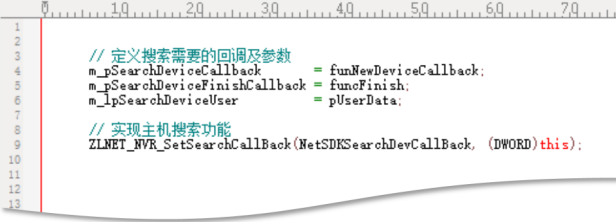
Woshida
The convenience this method offers is that SDK tools are easily acquired, detection is accurate, and is with high compatibility. But surveillance host information can only be found with corresponding search functions provided by vendor.
2.3 Exhaustion Detection
With this method, a database of default COM ports of all vendors is established. To find the required surveillance host, all IP addresses within the databased must be exhausted first, then the surveillance host can be confirmed by finding the open COM port with telnet protocol.
The method discussed above is simple, but with less accuracy, because we couldn’t know beforehand if a COM port is default
3 Conclusion
The ways mentioned above do not require much manual operation, the surveillance host info can be obtained by using either of the three methods provided that the forensic software is connected to LAN, which provides much convenience for field investigators who need evidentiary data from the CCTV footage urgently. The technology has been integrated in our key DVR forensics product, VIP(Video Investigation Portable).
