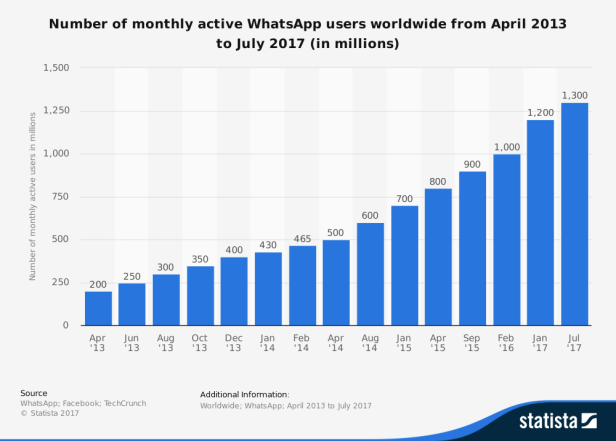
Editor’s note: WhatsApp is one of the world’s most popular instant messengers of smartphone applications. Today over 1300 million monthly active users exchange free messages with WhatsApp worldwide. (Statistics of Jul.2017) Based on whisper systems communication protocols, its point-to-point communications remain securely protected even if someone manages to intercept them. And apparently, these data could contain vital case-relevant information for investigators, which is why WhatsApp has become one of the most important focuses in the field of mobile forensics. However, it is common knowledge that investigations with smartphones are not always easy. Investigators could run into various types of difficulties during the process (database encryption, system securities, deleted messages, etc). So in this article, we will talk about how to decrypt encrypted WhatsApp database, how to bypass WhatsApp encryption, and how to recover deleted WhatsApp messages.
Part I: How to decrypt encrypted WhatsApp database?
Same as many other smartphone Apps, WhatsApp stores data in SQLite database files. For Android devices, there are two most important databases of WhatsApp, msgstore.db containing chat history, and wa.db containing contact lists. It is easy to get hands on these database files because WhatsApp has a backup feature, which creates database backup to the SD card, allowing access without any privileges like root. However, there is a serious problem for the law enforcement investigators, with recent security updates, WhatsApp databases are encrypted and cannot be analyzed directly. The chats, messages and call logs are using industry-standard AES-256 encryption, the media files like photos and videos are not encrypted. And the encryption updated from Crypt5, Crypt7, Crypt8, to Crypt12.
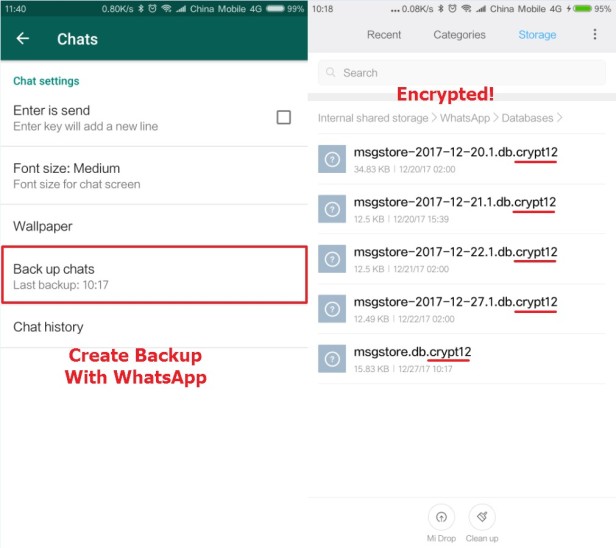
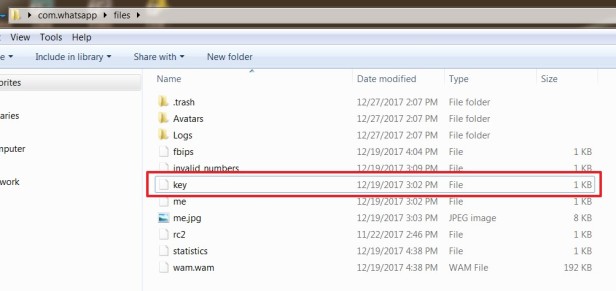
So how can we decrypt encrypted WhatsApp databases? The most important step is to get the cipher key. The cipher key is generated along with the WhatsApp backup when the first time the user made, the key is never stored in the cloud, instead, it’s only kept on the smartphone and it’s unique for each smartphone. So in order to decrypt an encrypted database, we must first extract the cipher key from the device where the backup is created. The cipher key can be found at the following location: userdata/data/com.whatsapp/files/key
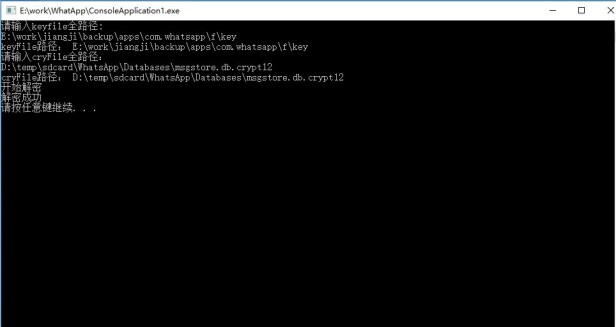
Now with the research of SalvationDATA forensic experts, we’ve developed a special algorithm to use the key file to decrypt encrypted WhatsApp database. We’ll soon release this tool and integrate into SmartPhone Forensic System(SPF), allowing investigators to deal with WhatsApp database encryptions without knowing any computer programing knowledge. A user simply needs to import the key file and the encrypted database, and the program will generate the unencrypted database file accordingly.
Part II: How to bypass WhatsApp encryption?
However, getting the key file is not always easy without rooting the device. So in this part, we’ll discuss how to bypass WhatsApp encryption, in other words, how to extract WhatsApp data without root access.
The key file and unencrypted database are always stored in WhatsApp’s folder. If investigators can get hands on these files, they can view all the WhatsApp communication histories on this device. The only problem is that they have no direct access to these files without root.
There are basically two ways to extract WhatsApp data without root.
1. System Backup & Restore
One way is to make use of Android system’s backup & restore feature. Many Android phone manufacturers allow users to create a backup with built-in system applications. Backup files created this way are stored in the SD card and unencrypted. So this is an easy approach for law enforcement to get access to the WhatsApp communication histories.
Below picture shows an example of using an OPPO smartphone to create WhatsApp backups. Users can find Backup Restore in Tools, create a new backup and remember to select WhatsApp.
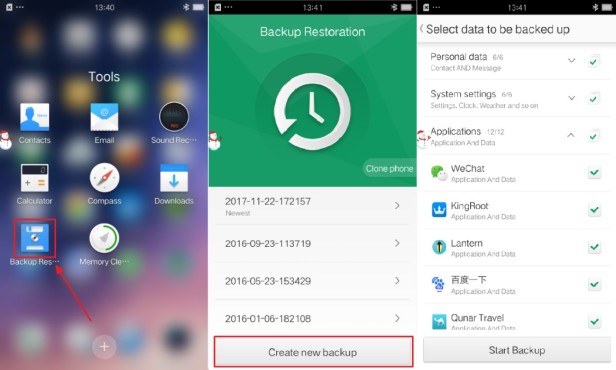
And then we can find the WhatsApp backup on the phone’s SD card. This backup will include all unencrypted databases and the key file of WhatsApp. Now, all we have to do is to analyze the database with a mobile forensic tool.
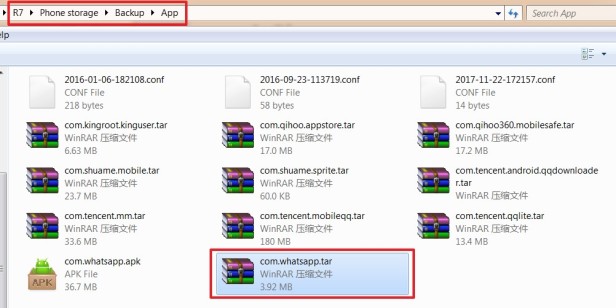
2. Downgrade Backup
Another way is to downgrade the WhatsApp application to a version that has no backup encryption feature. WhatsApp v.2.11.431 is the last version of WhatsApp without forced backup encryption. So the trick is to downgrade WhatsApp to v.2.11.431 without deleting the user’s data, then create a backup file with the old version WhatsApp and extract databases.
This process requires professional skills and has a risk of losing the data forever. Therefore, it is strongly recommended to use professional forensic tools to carry out a downgrade process.
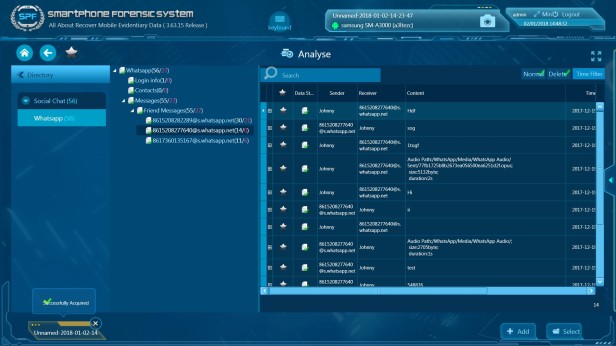
Part III: How to recover deleted WhatsApp messages?
Now we have known how to extract WhatsApp database files from a smartphone, let’s continue our topic to see how can we make use of the database files and recover deleted WhatsApp messages on both Android and iOS devices.
There are two ways for a user to delete WhatsApp messages. The messages can be deleted one by one or cleared all at once by using the clear/delete chats button. According to our tests, messages deleted in either of the ways mentioned above can be recovered using our method below.
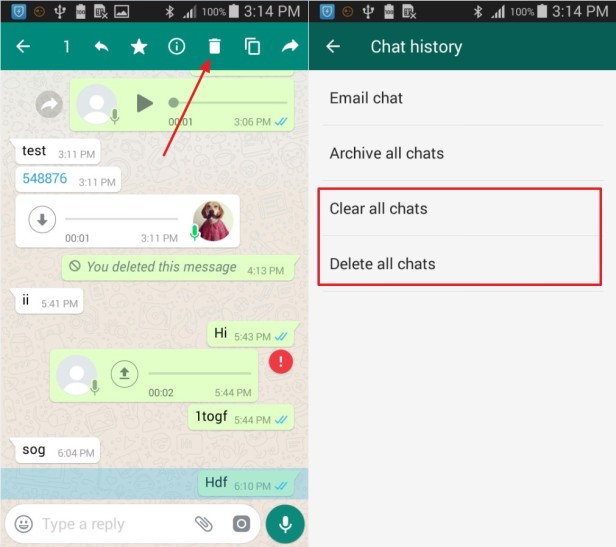
As we have introduced earlier, WhatsApp uses SQLite database to store its messages. But unlike Android, iOS stores all relevant WhatsApp data in one database called ChatStorage.sqlite. And these database files usually come with cache files with the suffix “-wal”. In most of the times, the size of these cache files is 0, but when it’s not, the cache files could contain important data that has not yet been stored in databases. This kind of situation must be handled carefully because if we leave the cache files unattended, information stored in it will be overwritten and lost forever.
According to our analysis, the normal accessible WhatsApp messages are stored in msgstore.db, while deleted messages are stored in msgstore.db-wal, which is the cache file for message storage. WhatsApp will always store the messages first in the cache file before saving it to the real database.
It is interesting that sometimes the cache file is even larger than the database file itself. This is because one message will only be stored as one record in the database, while there is no such limitation in the cache file. There could be multiple records of one message existing simultaneously. This makes it possible to recover deleted or lost WhatsApp messages.
However, in order to avoid overwritten data stored in the cache file, we must NOT open the database directly before we have properly handled the cache file. We must deal with the cache file first, by matching signatures, saving and analyzing all data from the cache file.
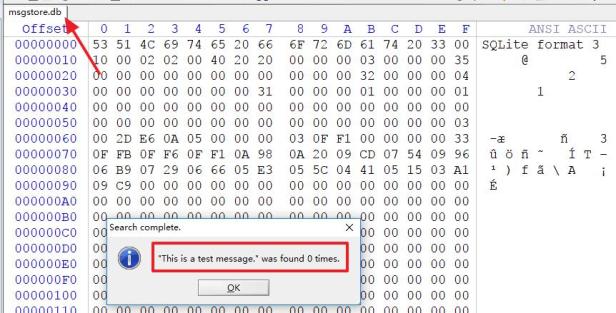
Let’s take a message record, for example, this is a test message. After the user deletes this message, the record of this message will usually also be wiped from the msgstore.db database file.
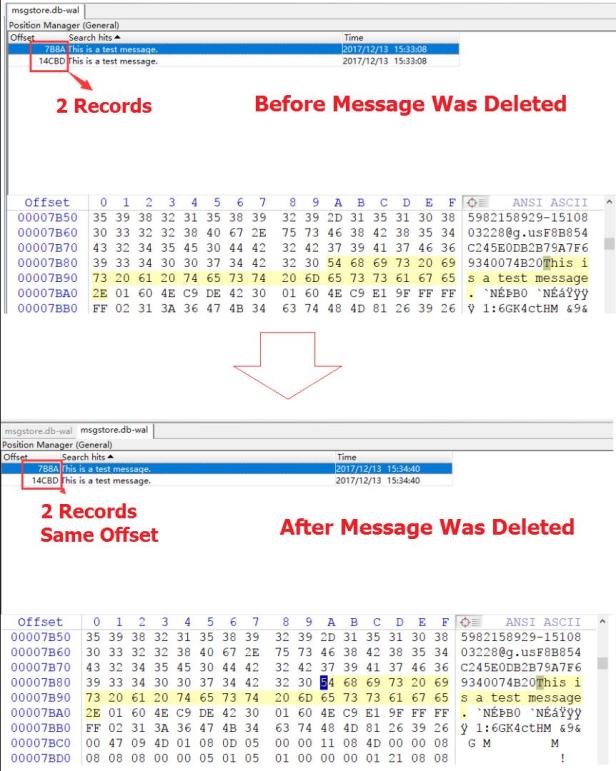
However, there may still be records of this message stored in the cache file msgstore.db-wal. Below picture shows an example of what happened before and after the message: This is a test message, was deleted. As we can see, after the message was deleted, the data of this message still remains in the cache file, and even the offset position of this record is not changed.
So by analyzing and extracting data from the cache file msgstore.db-wal, we provide solutions to recover deleted or lost WhatsApp messages. This solution mentioned above proves to be an efficient and reliable way to extract deleted WhatsApp data, a perfect solution for deleted messages and cleared chats histories.
Conclusion
With the research of SalvationDATA forensic experts, we can decrypt the encrypted WhatsApp database on Non-Rooted Android devices and recover the deleted WhatsApp messages on both Android and iOS devices. Please be noted that all the technology and solutions mentioned above are already or soon will be released and integrated into SmartPhone Forensic System(SPF). We hope this article will somehow help the DFIR community to deal with mobile devices to retrieve the evidentiary data as much as they can. We will see you soon with more practical forensic solutions.

what about a formated smart phone but with partial backup
赞赞
Hello, sir, we can use our mobile forensics SPF to recover and extract.
赞赞
Re: the following:
“In most of the times, the size of these cache files is 0, but when it’s not, the cache files could contain important data that has not yet been stored in databases. This kind of situation must be handled carefully because if we leave the cache files unattended, information stored in it will be overwritten and lost forever.”
Does “unattended” include leaving the phone on and allowing WA to perform regular maintenance? In this case leaving data unattended would be more of a forced activity, because you may be using the device during an examination. Also, if a significant amount of time passes between the last power down, and powering up of the device, does the time lapse have an impact on preserving wal data (if present in the first place)?
赞Liked by 1 person
Thanks for your comment!
This part of the post is discussing a way to recover deleted WhatsApp data from the SQLite database cache file. By ‘unattended’, we mean to remind the reader to extract valuable existing data from the cache file before operating on the database file. The cache file of a SQLite database is a temporary storage place for WhatsApp data, and can easily be overwritten. In a WhatsApp forensic work flow, it is recommended to first acquire and preserve both database and cache files of WhatsApp, then analyze and extract data from the cache file before opening the database file. And to your first question, yes allowing WA to perform regular maintenance may lead to data lost in the cache file. This is why the cache file must be handled with care in a forensic case. Second question, in theory cache file will only be updated when the database files are modified, so powering off for a long time should not have impact on preserving wal data.
If you are interested in our products, please send an email to [email protected]
赞赞
Quick question, everytime I edit an older message, Whatsapp find it corrupt? Is this normal behaviour? Is there a way to bypass this?
赞赞
Hi dear,
This article is focusing on recover deleted messages on WhatsApp.
So you can send your question to WhatsApp online service people.
Thanks!
赞赞
Hello, what program can I use to read and analyze a msgstore.db-wal?
Regards
赞赞
This “msgstore.db-wal” is a SQlite database file, which you can use our SPF Pro to do analyze, Please send trial request to [email protected]
赞赞
Thanks for your comment!
赞赞