Editor’s note: At the beginning of this month, we held a webinar talking about the forensic technics to extract WhatsApp data, bypass WhatsApp security mechanism, and decrypt encrypted WhatsApp database files. And we released a free forensic tool that is capable of decrypting the database and extract an unencrypted database of WhatsApp. In this article, SalvationDATA forensic experts will explain how to use this free tool to acquire important evidentiary data from WhatsApp.
If you missed our webinar, check out our webinar recording on our YouTube channel. Or read our WhatsApp forensics article, it may help you solve your problems.
Now let’s see how to use this free tool to carry out a WhatsApp forensic workflow.
I. Extraction or decrypt WhatsApp database backup
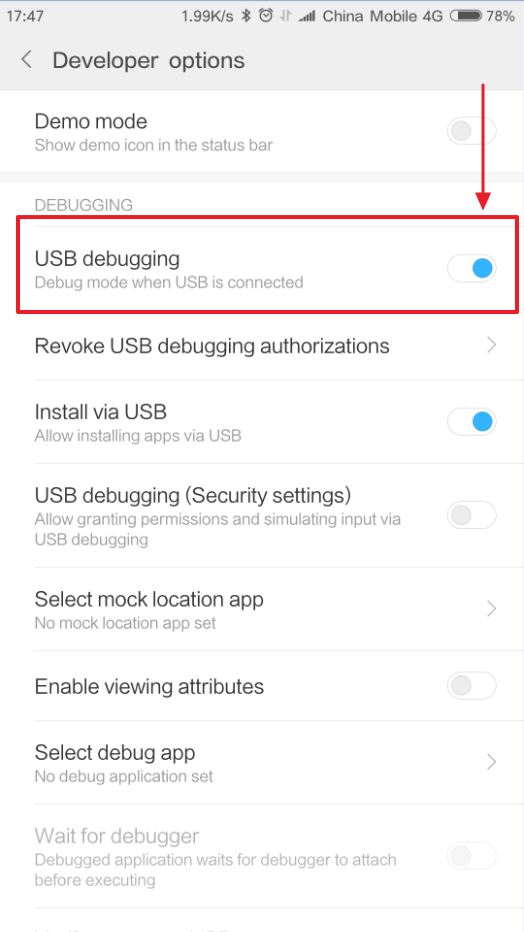
Step 1. Connect your smartphone to the PC with USB debugging enabled.
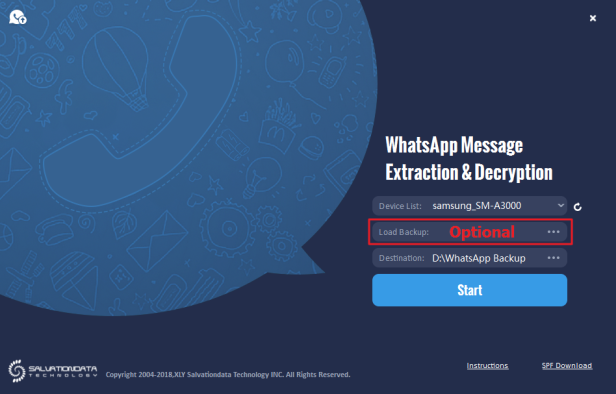
Step 2. Start the WhatsApp forensic tool, select the target smartphone from the device list.
Step 3. Set your destination path for backup file storage.
Step 4(optional). Load your encrypted backup. P.S. this step is optional, only load back up when you already have encrypted WhatsApp database files at hand.
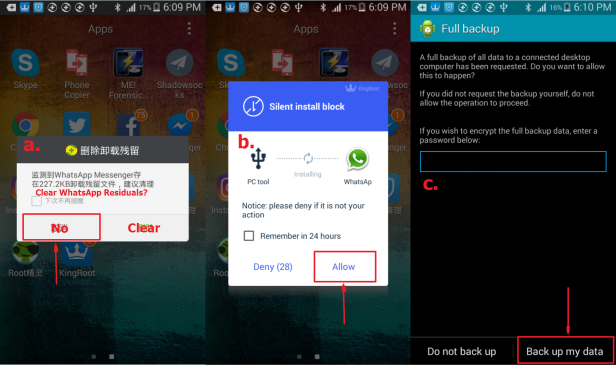
Step 5. Press Start and follow the instructions to proceed. Be extremely cautious,
- The tool will first delete the current WhatsApp application, make sure to press No if smartphone notifies you to clear residuals.
- Then the tool will install an old version WhatsApp, make sure to allow installation if a notification pops up.
- After downgrade successful, the tool will create and extract backup, press “Backup my data” to allow backup.
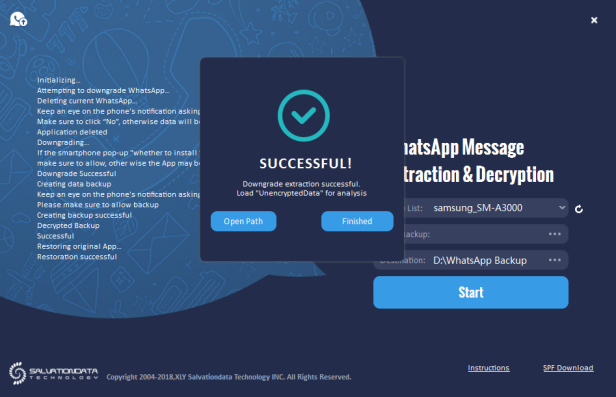
Step 6. After the backup is complete, wait for the tool to restore the original WhatsApp application and finish the process.
II. Load and analyze the extracted backup
Step 1. Start SPF(Smartphone Forensic System), or any other smartphone forensic tools you have that are capable of forensically extract and analyze data from smartphone backup files.
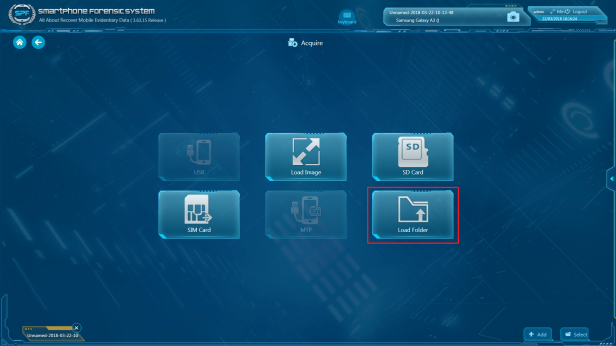
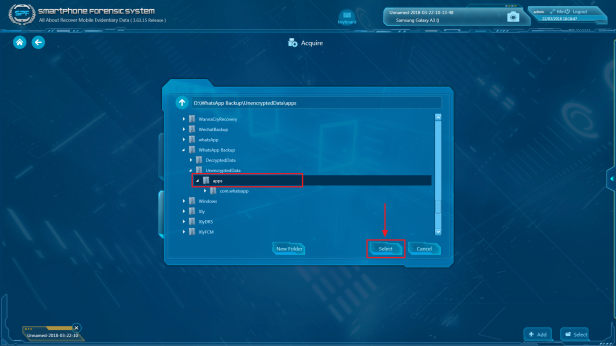
Step 2. Create Task-> Acquire, and in the source selection page, click “Load Folder”, and then set the destination path to where you saved the WhatsApp backup files.
P.S. Choose “DecryptedData” or “UnencryptedData” for analysis. Remember the target folder must be “apps” or “com.WhatsApp”, otherwise SPF will not be able to find WhatsApp data.
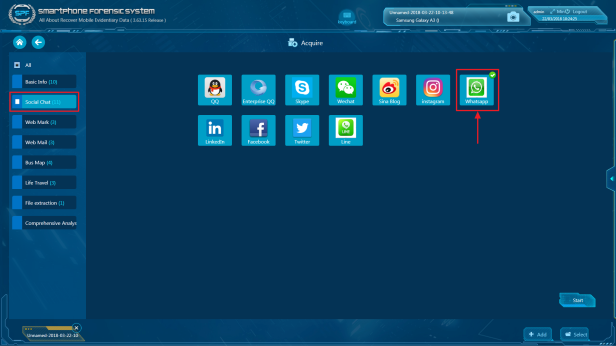
Step 3. Select WhatsApp for extraction and press “Start”
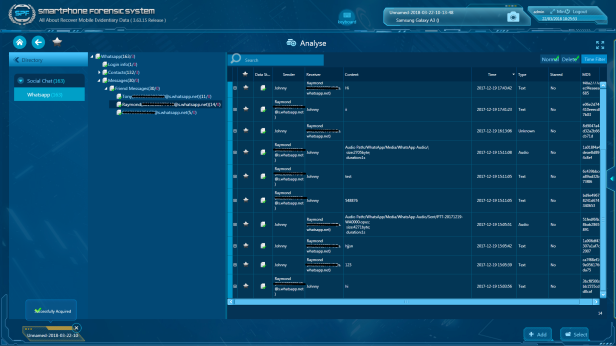
Step 4. Check out the extraction results and generate a report if needed.
Conclusion:
This article is an operation guidance on how to use SalvationDATA’s WhatsApp forensic tool and SPF to decrypt WhatsApp encryption and how to extract unencrypted WhatsApp backup from unrooted smartphones.
You can find the motioned tools form our resources page. Our WhatsApp forensic tool is completely free to use. We welcome all our customers to download this tool, and hope it could help the DFIR community to solve more cases!
