Editor’s note: With the continuous development of digital forensics technology, mobile forensics is no longer limited to the traditional way of extracting data exited in the cellphone itself. Data can also be extracted through network protocols. In this issue, forensic specialists from the Key Laboratory of Sichuan Province (collaborated with SalvationDATA) will explain how to extract mobile data from a router.
I Background Information
Cellphones are constantly receiving and sending data packets while accessing the network and numerous information on accounts, chats, files sent and received, e-mails and web-pages viewed are contained in these packets. Although much information is encrypted, a massive amount of information is transmitted in plaintext or can be decrypted through data analysis, this information including accounts, files, e-mails, and partial chats. Data can be extracted from router since all these data packets are distributed through it, at the same time saving the trouble of installing plugins on cellphones.

II Environment Building
Set up a router on a computer that has wireless network adapter by using the Bridge mode or by using the hotspot service provided by software like 360 Free Wifi. Data packets sent from cellphones connected to this router or Wifi can be captured.
III How to Capture Data Packets
Plenty capturing tools are available on the market and Wireshark is one of the well-developed ones that support brief data analysis after successful capture. All capture tools are developed on the same principle by using powerful programming interfaces of Wireshark and this issue explains network data packet extraction taking Wireshark as an example.
First, set all relevant parameters in software Settings’, as shown in Picture 1. To filter out irrelevant packets, a filter can be used if protocols are known. Moments in WeChat, for example, uses TCP protocol and port number 443 and 80, and this information can be used to set the filter. Then choose the network card that needs to be captured and begin the capturing process.

IV Network Data Packet Analysis
During packet extraction, Wireshark displays results in three different sections (Picture 2), the upper section displaying all the packets captured, the middle a brief analysis of the selected packet, and the lower the hexadecimal value of this packet.

For instance, one of the protocol packets, a complete chat packet of messages sent from the cellphone through WeChat is extracted in Picture 3. Based on the data in this packet, the cellphone (IP as 172.19.90.0, port number 51005) is transmitting data to the server (IP as 121.51.130.113, port number 80) through TCP-HTTP protocol.

The first three packets are those used to confirm ID between the cellphone and the server (TCP three-way handshake). The fourth packet contains the following information:
Frame: Data frame information of the physical layer
Ethernet II: DDL Ethernet frame header, including information on MAC addresses of the sender and the receiver
Internet Protocol Version 4: IP packet header in Internet layer
Transmission Control Protocol: Data segment header in transport layer, here as TCP protocol
Hypertext Transfer Protocol: Application layer protocol, here as HTTP protocol
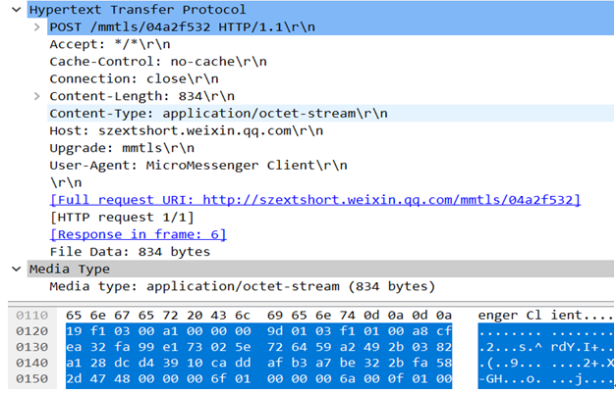
Media Type: Data transmitted

Shown in Picture 5 are contents of the application layer and the data layer, in which the followings are contained: the domain name of the server as szextshort.weixin.qq.com, information submission address as /mmtls/04a2f532, and data length of the data layer 834 bytes. The blue area of the hexadecimal panel displays the data sent, which is complexly encrypted and inaccessible.
Other data such as pictures and videos sent can also be analyzed in the same manner, and data extraction after successful capture can be realized through codes.
Conclusion:
Router packet capture is a brand new method to extract data and a key direction for future research that bears practical importance. Forensic specialists from the Key Laboratory of Sichuan Province (collaborated with SalvationDATA) already developed relevant application to capture and analyze network data packets. This application supports the analysis of various protocols and has already been integrated into our mobile forensics solution SPF(Smartphone Forensic System), you can download the software from our resources page of the website and have a free trial now.
