In this issue, data recovery experts from the Key Laboratory of Sichuan Province will introduce fast decryption methods for BIOS encrypted Hitachi hard drive. This method, compared with other commonly used methods, features simple operation, simplified process and high success rate, and can be used to help onsite forensic experts to quickly extract important clues.
Hitachi Global Storage Technologies (Hitachi GST) was founded in 2003 as a strategic consolidation of IBM and Hitachi, and hard drive manufacturing is one of the five Hitachi core businesses. Hitachi manufactures hard drives suitable for company and home use, and mobile hard drives. And, it occupies high market share in China.Data inaccessibility (with model number, LBA value and SN number recognized) for BIOS encrypted Hitachi hard drive is a problem onsite forensics staff often encounter during field investigation. This is because Hitachi hard drive users, to prevent leakage of hard drive data, set BIOS passwords in the computer mainboard while the computer boots, which causes the data inaccessibility problem for forensic experts and affects efficient case solving. Therefore, researches on decryption methods for BIOS encrypted Hitachi hard drives (here refer to hard drives for desktops and laptops, mobile hard drives are excluded) bear great importance.
I Introduction to Hitachi Hard Drives
1. Hitachi Hard Drive Structure
Hitachi hard drive consists of three parts: circuit board (including ROM information and NVRAM information), disk, and head. NVRAM (non-volatile random access memory, non-volatile refers to the ability to store data after power-off) is the 8-bit serial access Flash ROM chip on PCB (printed Circuit Board). NVRAM data are of great importance, and NVRAM of a Hitachi hard drive contains essential information such as number of heads, starting position of firmware area, verification for ROM overlay module, and disk adaptation parameters.
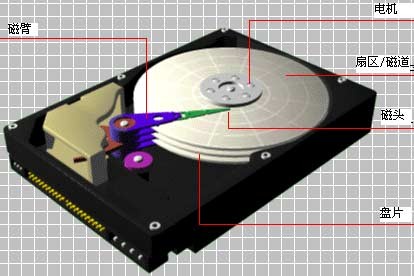
Hitachi hard drive structure
The above-mentioned information, number of heads, starting position of firmware area, verification for ROM overlay module, and disk adaptation parameters, are stored in ROM or disk firmware zone for normal hard drives, while Hitachi hard drives use NVRAM as its storage medium for these essential data. Apart from that, it also added another important feature: random firmware starting positions are allocated for each hard drive and are stored in NVRAM (it means that it is impossible to find two hard drives that have identical firmware stating positions). This feature indicates that every hard drive works only with corresponding NVRAM and loss or damage of NVRAM data can cause unrecognition of the hard drive by operating systems and utility software. Access to operation in the hard drive firmware zone is also inaccessible with incomplete NVRAM data, which means that the hard drive is paralyzed, let alone hard drive maintenance or data recovery.
2. Hitachi Hard Drive Firmware Structure
Hitachi hard drive firmware is mainly stored on the platter and, for both ARM and IRM Hitachi hard drives, firmware has two back-ups, Group A and Group B. Moreover, Group C, a back-up for Group A contained in Hitachi hard drives, is generated during auto-calibration when the drive is manufactured and cannot be changed or used. Even when both Group A and Group B are damaged for a disk, Group C will not be automatically enabled to replace A and B. Under these circumstances, specialized software is needed to access Group C, rebuild A and B, repair the hard-drive, and realize data recovery.
II Essence of Hitachi Hard Drive BIOS Encryption
In essence, Hitachi hard drive BIOS encryption is ATA password (data access lock) set by its user and recorded in the password module. There are generally three kinds of Hitachi hard drive password modules, IECS, SECI, and PSWD, and all professional tools can access and unlock these password modules through their password removal function. Hitachi hard drive, however, uses a more rigorous password protection measure: once a hard drive is locked in its user mode, all passageways to firmware zone will be locked and cannot be unlocked through reading its password module. In addition, Hitachi hard drives, different from those of other brands, record no plain text ATA password in their password modules.Encrypting the hard drive in its user mode is actually modifying the password module under Group A in user mode, after which Hitachi hard drive enters encryption status. Encrypted firmware zone under user mode provides no access to its data area.
III Methods for Hitachi Hard Drive Decryption: Access original password module under Group C through security mode
After analysis, data recovery experts from the Key Laboratory of Sichuan Province concluded that Group C in encrypted Hitachi hard drive is not modified or encrypted. Accessing the original password module under Group C through security mode and using it to recover Group A and B, therefore, can decrypt the hard drive and recover data. The following introduces Hitachi hard drive security mode and its accessing method.
1. Two Modes of Hitachi Hard Drives
Hitachi hard drives have two modes: user mode and factory mode; the former boots firmware and initialize the hard drive from Group A and the latter from Group C. Under encrypted status, the hard drive needs to be changed from user mode to factory mode to provide access to firmware zone, which is also a process to switch between Group A and Group C.
2. Method for Accessing Security Mode
Changing a Hitachi hard drive from its user mode to its factory mode requires setting of jumper wire and switching the hard drive to its security mode (i.e. work under circuit module). Switching from factory mode to user mode can be realized by modifying the starting mark byte in NVRAM without setting of jumper wire.
IV Decryption Process for Hitachi Hard Drive
The first step for decrypting a Hitachi hard drive is entering factory mode, which is usually referred to as security mode and provides access to firmware under Group C. Thus, the factory mode starting mark, recorded in NVRAM information in Hitachi hard drives, must be known.
After gaining access to firmware under Group C, read its password module and rewrite this module under Group C back to A and B. Any storage address offset of the password module appeared in A and B will lead to failure in module rewriting and then hard drive decryption.

Sketch Map for Hitachi Hard Drive Decryption Process
V Two Effective Factors of Successful Hitachi Hard Drive Decryption
Firstly, address offset of the firmware zone will lead to failure in accessing and rewriting password module; secondly, for Hitachi hard drives, failure might appear in entering its specific security mode and accessing firmware under Group C.
Conclusion
Data recovery experts from the Key Laboratory of Sichuan Province come up with methods that can successfully decrypt Hitachi hard drives through the following steps: access NVRAM chip under security mode; modify the starting mark of firmware zone; and rewrite the password module in Group C to Group A and B. This method can address the problem of data inaccessibility of BIOS encrypted Hitachi hard drives and is currently used in SalvationDATA DRS(Data Recovery System) and HD Doctor for Hard Drive Firmware to provide technical support for digital forensics.
Click HERE to learn more about DRS.
