Editor’s note: In this article, SalvationDATA forensic experts will explain the process of forensic data extraction from Android emulator.
The Android emulator is a virtual mobile device running on your computer. The software emulates an Android device, running the Android OS, for debugging applications without needing a variety of devices and OS versions. The Android emulator has various settings to make possible the emulation of a large set of Android devices, the common Android emulators are “BlueStacks”“Android SDK” and “MEmu”.

Analysis
MEmu Android emulator is based on VMware Workstation. It can export the virtual package with the “OVA” Image file, which contains all the necessary information. After researching and analyzing the “ova” image file, we found that the “OVA” image file is a compressed file. After we extracted it, there is a “VMDK” virtual disk file. Therefore, the data extraction and analysis of the Memu Android emulator only need to export the “VMDK” virtual disk file from “OVA” image file.
How do we acquire virtual disk file?
I. Direct extraction
After the Android emulator is installed, the virtual disk files are generated by default in the installation folder. These files can be analyzed by the SalvationDATA DF(Digital Forensics System currently available in China only).

II. Extract “VMDK” virtual disk file from”OVA” image for analysis
After decompressing the “OVA” image, you can directly get the “VMDK” virtual disk files, and then use any forensic tool to extract the data and analysis.
Now let’s see how to extract data from Android emulator by using our DRS(Data Recovery System) and SPF(SmartPhone Forensic System). You can download them from our resources page of the website and have a free trial.
Case Study with Tencent QQ application
Step 1. Load “OVA” image file into DRS to extract and recover all “OVA” format files and save them to local

Step 2. Change all “OVA” image file to compressed format files, then decompressed them to acquire “VMDK” virtual disk files.

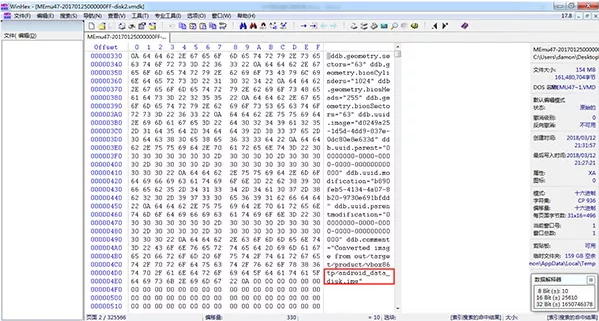
Step 3. Load “VMDK” virtual disk file into WinHex and locate the data area
Step 4. After locating the data area, load “VMDK” virtual disk file into DRS to extract the QQ application data package “com.tencent.mobileqq” folder and export it to the local

Step 5. Use the above method to recover and export the “Tencent” folder and save it to the same destination of “com.tencent.mobileqq”

Step 6. Finally, use SPF to extract and analyze the QQ chat history related to Android emulator

Conclusion:
When extracting the data from Android emulator, we need to find the virtual disk files and use the smartphone forensic tools to analyze the data.
