Editor’s note: Apple is known for their continuous efforts to make their user’s private data secured. I believe the news that Apple enhanced USB restricted mode in iOS 12 has already became a hot spot in the DFIR community.
If you are a police officer, a law enforcement investigator, this is grave news for you. So today, SalvationDATA forensic experts will talk about iOS USB restricted mode, we’ll see what is USB restricted mode, what does it do, what enhancement has been made in iOS 12 and how are they going to have an impact on our works.
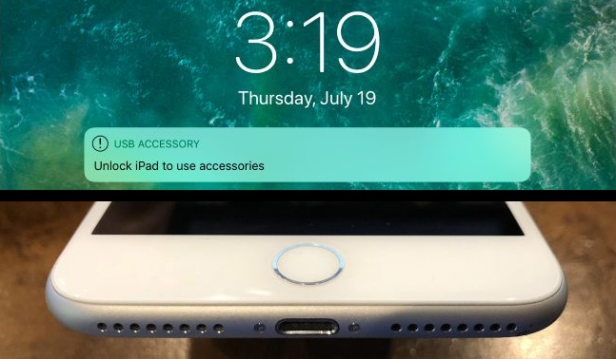
What is USB Restricted Mode?
The USB Restricted Mode was first introduced in iOS 11.4.1. USB Restricted Mode prevents USB accessories that plug into the Lightning port from making data connections with an iPhone, iPad, or iPod Touch if your iOS device has been locked for over an hour. This seemingly small change goes a long way in blocking tools used by law enforcement to crack passcodes and circumvent Apple’s encryption and built-in measures designed to shield sensitive user data.
Actually Apply has never said as much it, but it’s believed that USB Restricted Mode is Apple’s effort to combat forensic devices that are specially designed to help law enforcement crack an iOS device’s passcode and retrieve data that would normally be guarded by encryption. iOS has built-in security features that prevent constant passcode guesses — such as when it locks down your device after several incorrect attempts. But of course, this would not stand in the way of forensic solution providers, some companies have seemingly found a way of avoiding those safeguards via USB and the Lightning port. Now, Apple is trying to eliminate this method of gaining entry to a recovered or confiscated device.
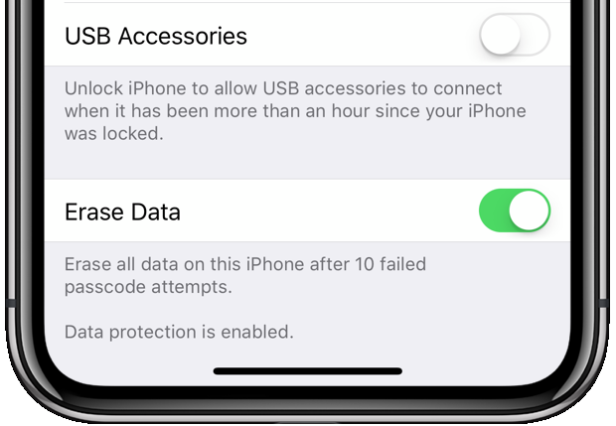
What does USB Restricted Mode do?
Once USB Restricted Mode is engaged on a device, no data communications occur over the Lightning port. A connected computer or accessory will not detect the iPhone as a “smart” device.
USB Restricted Mode works like this: after an hour of your iPhone, iPad, or iPod Touch sitting without being unlocked, iOS will basically cut off the Lightning port and limit it to charging only. This hour timeout should theoretically stop forensic devices (which plugs into an iPhone and cracks the passcode within a few hours) from working successfully.
So, USB restricted mode effectively deters the ability of third-party forensic tools to crack iPhone’s passcodes.

What enhancement has been made in iOS 12?
According to Apple itself, the additional security measures were required because “the USB accessory ecosystem doesn’t provide a reliable way to identify accessories before establishing a data connection”.
Below is a brief summary of USB Restricted Mode in iOS 12. In iOS 12, USB Restricted Mode engages if any of the following conditions are met:
- One hour after the phone is locked, or one hour since the phone was disconnected from a USB accessory (whichever is later). Basically, one hour since last unlock/last disconnect.
- Immediately after the phone is locked if 72 hours or more have passed since the phone last established connection with a USB device. If the 72 hours have passed, USB Restricted Mode will engage immediately every time the iPhone’s screen is locked.
- After S.O.S. mode
- If the iPhone is in a state where it requires a passcode to re-enable biometric authentication (“Your passcode is required to enable Touch ID/Face ID” message is displayed); basically, USB Restricted Mode now engages under the same rules as Touch ID/Face ID expiry.
Is there a solution to crack USB Restricted Mode?
Actually, merely plugging in nearly any device (not just ones that have previously been connected to that phone), such as Apple’s Lightning to USB 3 Camera Adapter, will disable the one-hour limitation. This would give a forensic inspector enough time to bring the device to a lab and then work on it for as much time as they’d like.
The problem likely lies in Apple’s Lightning communication protocol — in other words, the way the iPhone “talks” to devices that are plugged into it. When you connect the iPhone to a computer, the two devices exchange cryptographic keys and establish trust. Many Lightning accessories, however, don’t have the capability to do that, so the iPhone just trusts them by default.
If this is indeed a bug and not intended behavior, it might be hard for Apple to fix it. A fix could render numerous Lightning accessories useless — though it might be possible to make sure the iOS device only communicates with devices that were previously plugged into it.
Conclusion
The iOS 12 update brings additional challenges to our forensic works. But of course, we, digital forensic solution providers, are also making continuous efforts to catch up with the rapid developing private data security technologies. Check out our website and see what forensic solutions we offer. Keep following our blog posts for the latest DFIR news and updates!
