Editor’s note: ADB (Android Debug Bridge) is a very common and one of the most basic mobile forensics tools to deal with Android devices. In this article, forensic experts from SalvationDATA will have a quick walk through of one of the most practical utilities from the ADB toolkit: ADB backup.

What is ADB?
ADB (Android Debug Bridge) is a versatile command-line tool that lets you communicate with an Android device. The adb command facilitates a variety of device actions, such as installing and debugging apps and extracting user data from the device.
ADB’s use in forensics.
An interesting fact that always manages to surprise people when we tell our customer is that Android is based on the Linux kernel and you can even pull up a command-line shell (with standard Linux commands!) using certain applications. Furthermore; forensic examiners can utilize the ADB tools, which enables them to connect with an Android device from a host system, traditionally via a cable connection. As per the official developer page, ADB is capable of; “a variety of device actions, such as installing and debugging apps, and it provides access to a Unix shell that you can use to run a variety of commands on a device”.
There are many useful ADB utilities that can be used to help a forensic investigation, today we’ll talk about one of the most important sets of utilities in ADB tools: ADB backup.
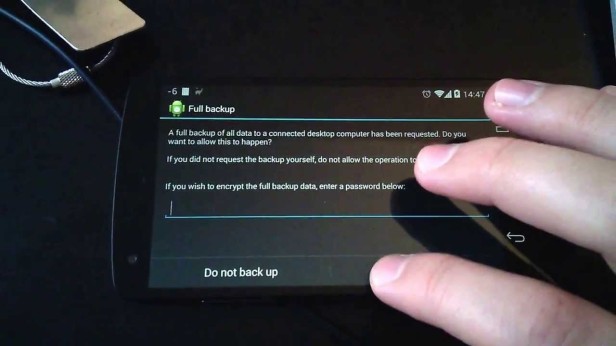
ADB Backup
The ‘abd backup’ command is commonly utilized when performing a logical extraction of an Android device. In digital forensics, the term logical extraction is typically used to refer to extractions that do not recover deleted data, or do not include a full bit-by-bit copy of the evidence, analogously to copying and pasting a folder in order to extract data from a system. So, this process will only copy files that the user can access and see: if any hidden or deleted files are present in the folder being copied, they will not be in the pasted version of the folder.
Generally, a standard user might use ADB to back up their device data, which they can restore at a later time. And when you are doing a mobile forensic investigation, it can help you pull data from an Android device.
A full adb backup command line can include below elements:
-f <file>.ad: Write an archive of the device’s data to a specified *.ab file.
-apk: Enables backup of the *.apk files themselves.
-shared: Enables backup of the devices shared storage/SD card contents.
-all: Enables backup of all installed applications.
-system: Includes backup of system applications (enabled by default).
-obb: Includes backup of any installed apk expansion (.obb) files associated with each application.
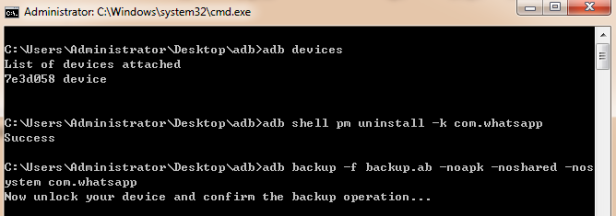
Once the device was detected by ADB, the backup command can be executed. Upon running this command, the device prompted for confirmation. It should also be noted that if your Android device is encrypted, the backup will not proceed unless it is also encrypted with a passcode set by the examiner.
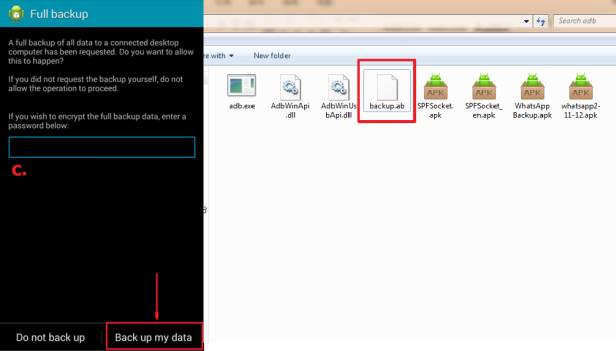
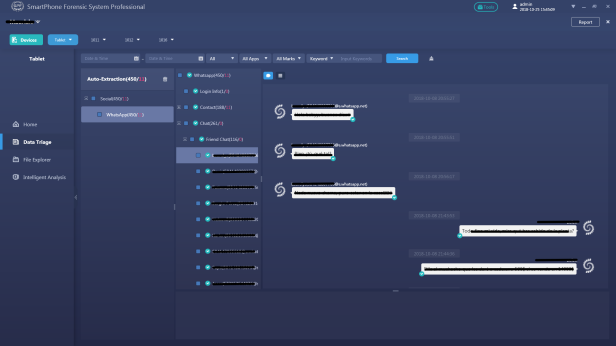
Once we have generated a backup file of the Android device, the backup file is in .ab format and can be imported into a preferred analysis tool to parse the data and present it in a readable format, such as SalvationDATA’s mobile forensic system SPF Pro (SmartPhone Forensics System Professional).
SPF Pro supports to load and directly analyze an ab format adb backup file, extract and present the acquired data in a way that is easy to read for forensic inspections.
Conclusion
If you are interested in our forensic solutions, come and check out our website for more information. You can also go to our resource page to download our forensic products for free. We welcome you to contact us and claim your free product trial!
