Editor’s note: You might hear about the dark web, but never really had a clue about it. Every time we mentioned the dark web, people get goosebumps. Unlike the known Internet, the dark web is a hidden network that cannot be found through the conventional web tools we use every day. And due to its property, the dark web has become a place where the outlaw and network crime happen. Today, SalvationDATA forensic experts will take you to the hidden corners of the Internet to introduce the dark web and Tor.
![[Case Study] Computer Forensics: An Introduction of the Dark Web and Tor](https://blogsalvationdatacom.files.wordpress.com/2019/05/1.png?w=616)
What is the dark web?
The internet is a much, much bigger place than you probably realize. Only a few parts of the network called “ internet” is visible by the general public. The Dark Web is a subset of Deep Web which could be significantly browsed by the terms of a specialized tool, the authorized permission, special configuration of a computer, it is distinguished from the surface web which can be searched by the ordinary searching engine.
![[Case Study] Computer Forensics: An Introduction of the Dark Web and Tor](https://blogsalvationdatacom.files.wordpress.com/2019/05/2.png?w=616)
Most of the sites spread on the Dark Web have hidden their identities through the Tor encryption tool. It is known that Tor would be used to hide your identity and activity. Using the Tor to spoof the actual location and the in-veracious one is similar to the method of using a VPN service.
What is Tor?
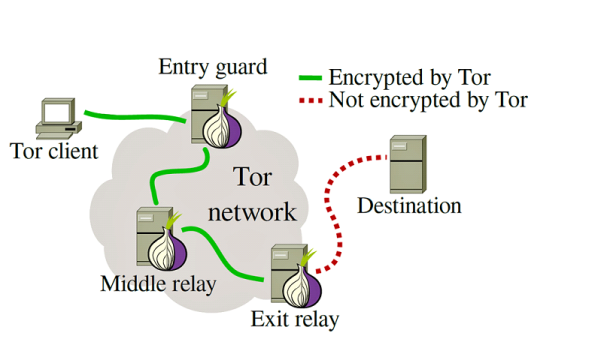
Tor is free and open-source software for enabling anonymous communication. The name is derived from an acronym for the original software project name “The Onion Router”. Tor directs Internet traffic through a free, worldwide, volunteer overlay network consists of more than seven thousand relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity to the user.
How does Tor work?
The Tor network runs through the computer servers of thousands of volunteers (over 4,500 at time of publishing) spread throughout the world. Your data is bundled into an encrypted packet when it enters the Tor network. Then, unlike the case with normal Internet connections, Tor strips away part of the packet’s header, which is a part of the addressing information that could be used to learn things about the sender such as the operating system from which the message was sent. Finally, Tor encrypts the rest of the addressing information, it is called the packet wrapper. Regular Internet connection doesn’t do this.
Each relay decrypts only enough of the data packet wrapper to know which relay the data came from, and which relay to send it to next. The relay then rewraps the package in a new wrapper and sends it on.
The layers of encrypted address information used to anonymize data packets sent through Tor are reminiscent of an onion, hence the name. That way, a data packet’s path through the Tor network cannot be fully traced.
Conclusion
In the beginning, the core principle of Tor, “onion routing”, was developed in the mid-1990s by the United States Naval Research Laboratory, with the purpose of protecting U.S. intelligence communications online. However, today the dark web and Tor technology have become the spear of network criminals. Protected by the anonymous mechanism, the dark web turns out to be the perfect marketplace for illegal transactions. As a professional digital forensic solution provider, SalvationDATA is now developing a new web forensic system, which can provide investigators with easy access to the dark web. Stay tuned for our news and updates!
