Editor’s note: Digital forensic investigators usually get headaches when they have smartphones locked by password, or even worse, phones cannot power up due to physical damages. When you run into a situation like this, what are your options?
Earlier we issued an article on our blog introducing a solution to physically extract evidentiary data from smartphones equipped with Qualcomm chipsets. It is realized by making use of a reserved test port to extract the physical image directly from a phone’s memory chip. This method is an effective and efficient solution for smartphones locked by password or with physical damages. But here is the question, does this work only for Qualcomm chipsets? Of course not!
MediaTek is one of the world’s leading systems-on-chip designer for mobile devices who holds one of the biggest shares of the smartphone chipsets market in the world. According to statistical data, Qualcomm and MediaTek combined took up almost 80% of the Android smartphone chipsets market in 2017. Smartphones with MediaTek chipsets also have a test port called the MTK pre-loader similar to Qualcomm, and can also be used for physical data extraction.
MediaTek(MTK) physical extraction solution is also integrated into our SmartPhone Forensic System(SPF). You can download SPF from our resources page of the website and have a free trial.

Now let’s see how to utilize the tool integrated with SPF to physically extract forensic images from smartphones equipped with MTK chipsets.
Step 1. The first step is always driver setup. In order for the test port: MTK pre-loader to be recognized by the operating system, the port driver must be installed in the first place. MTK USB driver can be found online.

Step 2. Open SPF (SmartPhone Forensic System) and select “Tools”.
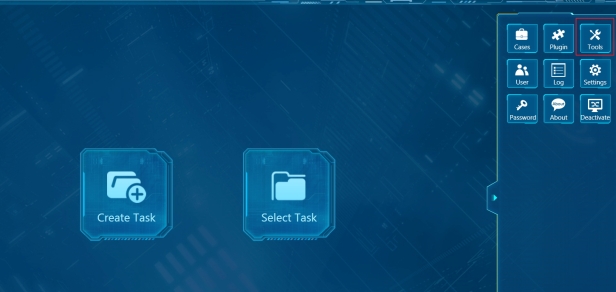
Step 3. Select “MTK SmartPhone Flash”.

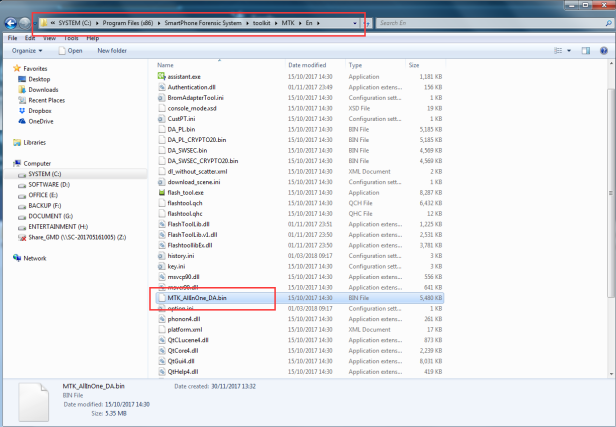
Step 4. Load file “MTK_AllInOne_DA.bin” from folder “SmartPhone Forensic System>Toolkit>En”.
Step 5. Load “MT6752_Android_scatter.txt” and select “preloader” only.
BTW: Common MTK scatter files are already included in SPF, but if you cannot find the correct scatter file for your device, search for it online.

Step 6. Go to “Memory Test” page>select “RAM Test” only>disconnect the phone from PC before we start to run memory test>Click “Start” and connect your phone to PC.

Step 7. When “Memory Test Ok” window pops-up then we can see there are a few partitions there, but we only need “EMMC_PART_USER”, so we copy the value numbers “0x0000000747c00000” and go to Readback page.

Step 8. Now, we are all set to create “Forensic Image”. Disconnect the device>click “Read Back”>Connect the device back to pc, and the Imaging progress will start immediately.

Step 9. Finally, MediaTek(MTK) physical extraction is done.
Well, this is the procedure we extracted data from locked MTK based Android phone, what can we get from this file? The answer is you can use any mobile forensic tool to import the file for data analysis.
Here, we give you an example of using SmartPhone Forensic System(SPF).
Step 1. Open SPF>Create Task>Load “Image File” from the path where we saved before>Click “OK” to go to next page and click “Acquire”.



Step 2. Select the items that you would like to acquire and Click “Start”.

Step 3. Now, we can start to investigate the case with SPF (SmartPhone Forensic System).

Conclusion: Based on the data analyzed in this demo, the SPF produce the excellent results in a physical extraction and forensic investigations also MTK SmartPhone Flash Tool provides more comprehensive steps for user operations and is considered to be highly recommended to the principle on digital forensics.
Here are following reasons:
1.The tool can extract full range of data even if the phone is password protected or USB debugging mode is disabled; or in the absence of root access.
2.The tool seamlessly provides an extraction method that can apply to all MTK Android smartphones, irrespective of the phone brands or models (the upcoming models are also included), which are running on the same designated MTK based CPU chipsets.
3.This technique developed by SalvationDATA also includes read-only functionality, ensuring that data from mobile devices is extracted in a forensically sound manner. We will never stop for developing technique, and help the DFIR community to deal with mobile devices more efficiency in mobile forensics.
