Editor’s note: We recently received a crime investigation support request, which is involved with WhatsApp backup database encryption. The artifact to be examined is an Amazon tablet installed with a Fire OS. A police officer turned to us for help because he found the WhatsApp backup database files are encrypted and show “Cypt12” after the filename. A SalvationDATA forensic engineer helped to make crucial progress to the investigation by providing both WhatsApp data on the tablet and chat history from the encrypted database files to the police officer. We posted this article hoping that it will help with your investigations by letting you know how to decrypt WhatsApp backup database files and extract important evidence data.

Case Introduction
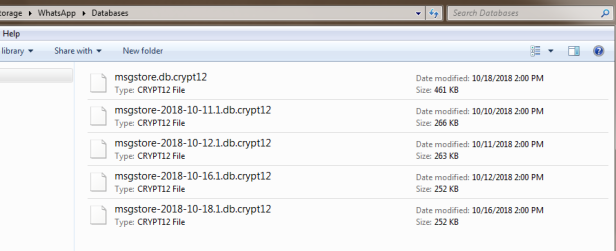
According to the police officer, this is a violence case. Of course, we don’t want to introduce any sensitive information here. Obviously, the first priority is for us to find out the suspect’s true identity. He appears to be someone that the victim knows. So the police officer checked the victim’s WhatsApp data on the tablet. Unfortunately, no suspect information was found. The key chat history might have been deleted because there were only chats for a few days on the tablet. The police officer then found WhatsApp database backups on the tablet SD card, which are created on 11th, 12th, 16th, and 18th Oct. These backups are highly possible to contain crucial case information because the time of incident it on 14th Oct. However, at the end of the file extension, it says “Crypt12”, which means the files are encrypted, this is when the police officer made contact with us.
Is it possible to extract data from encrypted WhatsApp backup?
The answer is yes! WhatsApp uses the AES algorithm to encrypt and protect its database backups stored in the SD card. And the cipher key to unlock this encryption is kept as a key file stored in the WhatsApp data folder under Android system user partition. So if we can somehow acquire the key file, and use it to complete a reverse calculation based on the correct algorithm, we can decrypt the WhatsApp backups. SalvationDATA developed a full set of solution to deal with this kind of situation and provide the forensic investigators with potential evidence data as much as possible.
If you want to learn more about WhatsApp backup encryption, and the solution to decrypt it, check out our early blog post below:
WhatsApp Forensics: Decryption of Encrypted Databases and Extraction of Deleted Messages on Non-Rooted Android Devices
And now let’s check out how exactly our forensic engineer help to get the WhatsApp data both from the tablet and the encrypted backups.
How to extract and decrypt WhatsApp data?
The Amazon tablet Fire OS, like all other Android OS, protects the user partition by setting restrictions to normal user access. Extracting WhatsApp data from the tablet and acquiring the key file to decrypt the backups both require direct access to the WhatsApp data folder stored in the user partition. So what we first need to do is to bypass the access restrictions. After a quick analysis of the situation, our forensic engineer decided to extract the WhatsApp data folder by a downgrade process. We are going to explain this process by using adb tools, you can easily find adb tools on the Internet and repeat our process.
Step 1.
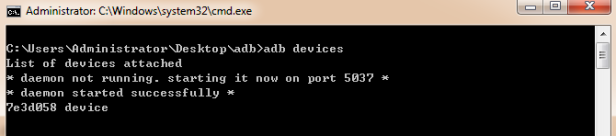
Connect the target tablet to the PC and run adb window. Use adb cmd line “adb devices” to verify the connection.
Step 2.
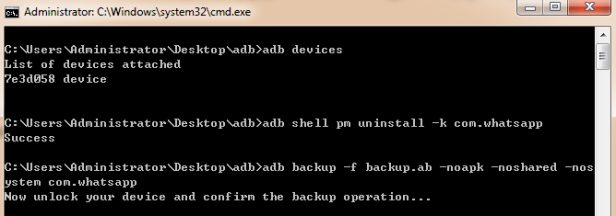
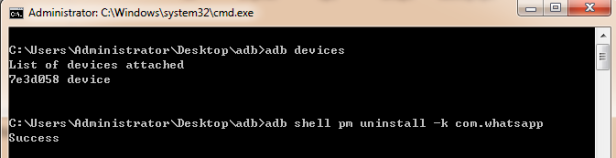
Now we need to uninstall the current WhatsApp application on the tablet because late version apps don’t allow adb backup. In the cmd line, “-k” must not be missed because it ensures that user data will not be deleted when uninstalling WhatsApp.
“adb shell pm uninstall –k com.whatsapp”
Step 3.
In order to extract the WhatsApp data, we must install a history version WhatsApp application, which would allow us to create unencrypted backup files with adb command. We can simply copy the apk file to the tablet, or use adb to complete the installation.
Step 4.
After all is ready, give the tablet a command to create the backup.
“adb backup –f backup.ab –no apk –noshared –nosystem com.whatsapp”
Step 5.
When the command is given, we’ll see a backup window on the tablet, simply click “Backup My Data” to continue. Then we’ll get a WhatsApp data backup in .ab format.
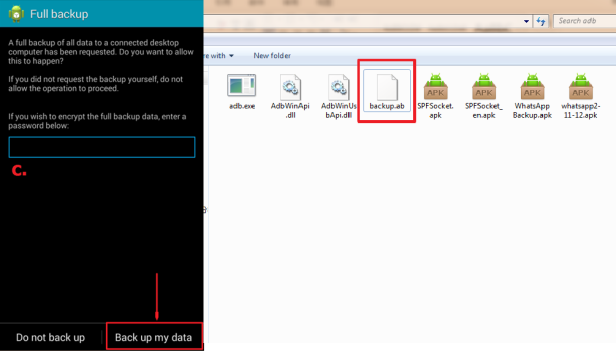
Step 6.
The .ab file is adb backup file format. It can be directly analyzed and extracted by using our SPF Pro (Smartphone Forensic System Professional).
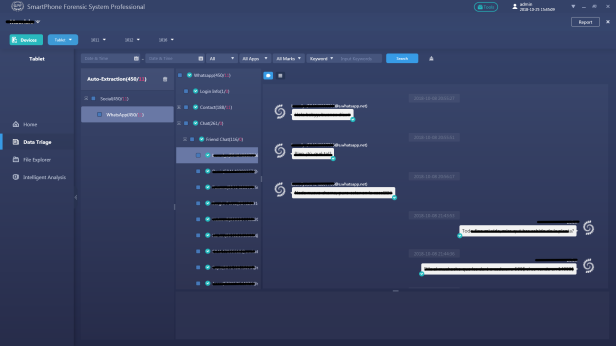
Step 7.
After extracting the .ab file, we also successfully located the key file. Now we just use it to decrypt the encrypted WhatsApp database files with SalvationDATA’s WhatsApp decryption tool.
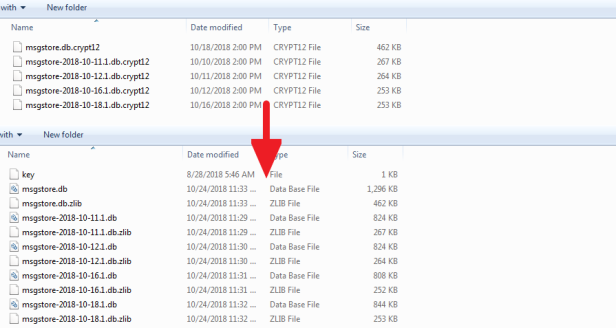
Conclusion
In the end, our forensic engineer got both the live WhatsApp data on the tablet and the backup data from the encrypted database files. By opening and processing the decrypted WhatsApp backups, the police officer found important clues and continued his investigation. We hope this article is going to help you know your options if you are currently struggling to get data from encrypted WhatsApp backups. Come and check out our website for more information. You can also go to our resource page to download our forensic products for free. We welcome you to contact us and claim your free product trial!
