Editor’s Note: Digital forensic investigation on mobile devices requires investigators to follow step by step workflow to extract and analyze digital evidence. In this article, forensic experts from SalvationDATA will continue to have a technical walkthrough on Android forensic data extraction using ADB to collect crucial device artifacts for digital forensic analysis and investigation.

Device Acquisition Procedure
Device Acquisition
The forensic acquisition is the steps of making a bit by bit replica of the custodian device while maintaining the integrity of the data stored in the device. Android devices however come with a two-level of access which an investigator has to determine in preliminary acquisition steps.
Understanding Level of Access:
Android devices offer two-level of access that are root or non-root access. Devices come pre-built with non-rooted access, Which allows investigators to perform logical acquisition instead of physical acquisition. In simple terms, whatever information is stored and available logically can be acquired.
Root accessed devices however offer a complete level of device access, which can also be determined as administrator access. Here devices can be acquired locally and physically. The logical partitions, system partitions, ram, and ROM are available for acquisition.
How to determine a device is rooted or non-rooted?
Using forensic utilities:
- Forensic utilities mostly available in the market are available for commercial purpose usage only. However, utilities such as Cellebrite, Oxygen, SPF Pro, etc. Software utilities provide stepwise methods to acquire an Android device.
- Forensic utilities can determine if a device is rooted or non-rooted hence moves forward with the method of acquisition as per the availability of the data.
Manual methods:
Device Prerequisites:
- The device should be unlocked
- USB Debugging Should be enabled
Machine Prerequisites :
- Minimal ADB Installation
- Steps to Check Root Access
- Close all the active connections by putting the device on flight mode
- Unlock the device and connect it to the workstation via USB cable
- Open CMD/Powershell(Windows) or Terminal (Linux/Debian/Mac OS) and execute the following commands
ADB devices
- A unique identifier with a device name should be visible.
- A popup will be displayed on the device consisting of RSA fingerprint key and confirmation to add the machine as a trusted device
ADB shell
- Shell access should be granted to the device
- A basic list of Linux commands such as ls, dd, cat, etc is usable in the shell
Su Command
- Checks if the device has superuser/root permissions.
- If permission is denied or command not found is displayed, the device should be non-rooted.
- Try accessing the system files & folders
a. Execute CD /data
b. Ls to view the files and folders present in the current directory
c. If LS returns no data, then the system files and folders are hidden. Which cannot be modified as it requires root permission. Hence, the device is non-rooted.
Traversing System Folders — (Non-Rooted Device)
Traversing System Folders — (Rooted Device)
Device Imaging
Device imaging can be performed once we have identified the device is rooted or non-rooted.
Rooted Device Acquisition
Devices with root access can be acquired using manual methods or using a forensic tool such as SPF Pro.
Manual Acquisition Method:
Once you enter as a root user, check for the mounted partitions-
- Cat /proc/partition
- Displays the available partitions with size in kilobytes. The files are stored in /dev/block/partition name
- Available partitions Android Partitions
Exploring the available partitions:
- Mmcblk0 : We can see that the partition has 15388672 KB size which is around 14.67 GB
- Mmcblk0p1 : Block Size — 20480 KB which is around 20 MB
- Mmcblk0p2 : Block Size — 1280 KB which is around 20 MB
- Mmcblk0p3 : Block Size — 1280 KB which is around 20 MB
- Mmcblk0p4 : Block Size — 8192 KB which is around 8 MB
- Mmcblk0p5 : Block Size — 8192 KB which is around 8 MB
- Mmcblk0p6 : Block Size — 8192 KB which is around 8 MB
- Mmcblk0p7 : Block Size — 204800 KB which i6s around 200MB
- Mmcblk0p8 : Block Size — 16384 KB which is around 16 MB
- Mmcblk0p9 : Block Size — 8192 KB which is around 8 MB
- Mmcblk0p10 : Block Size — 2097152 KB which is around 2 GB
- Mmcblk0p11 : Block Size — 11616256 KB which is around 11.07 GB
- Mmcblk0p12 : Block Size — 524288 KB which is around 512 MB
Using DD command we can acquire a memory block/partitions.
- Advanced DD commands such as DCFLDD or DC3DD aren’t available for most of the devices. It can be executed if the device owner has pre-installed DCFLDD or DC3DD binaries.
Execute the following DD commands:
- Dd if= source” of=”destination directory/destination file.dd”
- DD command can create a disk image on the device via manual method. You can insert a blank SD card to output the image file to the external SD card location.
- Sample command :
DD if=”/dev/block/mmcblk0” of=”/extSdCard/image/mmcblk0.dd”
Transfer the acquired memory blocks to investigation machine using ADB pull or direct file transfer using MTP:
![]()
You can transfer the image files by copying the files from the SDCARD using a memory card reader. Always ensure while transferring files from one source to a destination, a write blocker should be always active so that we can refrain from the modification of evidence. Software-based write blockers can be utilized or the memory card should be mounted in read-only mode.
Non-Rooted Device Acquisition
Devices with non-root access can be acquired using logical acquisition techniques. Non-Rooted Device can be temporarily rooted and acquired but the process tampers with the user data hence is not recommended. With limited access to the user device, non-rooted device acquisition techniques extract minimal data from an Android Device. The following steps enumerate the procedure to acquire a non-rooted device:
1. Discovering the device via ADB
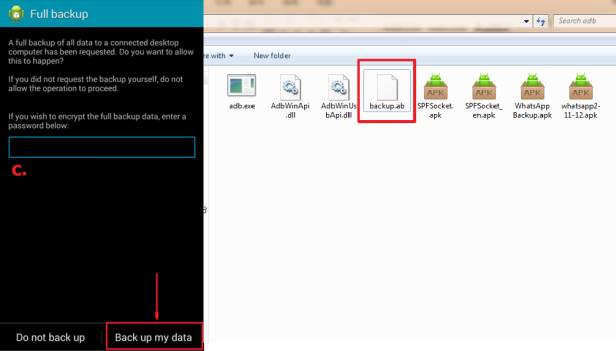
2. Executing ADB backup
3. Now accept the Full Desktop backup by entering a secure password
4. A backup file (backup.ab) gets created after the backup is successfully created
a. Executing Local Backups
- A local backup can be created in the device itself, it is much faster than ADB backup. However, an external SD Card is recommended to utilize for local backup storage.
- The following steps show how to create local backups.
b. Navigate to Device>Settings> Backup and Restore
c. Check for the available backup locations such as System setting and Application Data
d. Validate the selected items and start the backup process
- Local backups are created and stored in .bak file format
- Descript.xml file contains the backup file information.
- The local backup contains application and user data backup
Image Integrity
Device acquisition depends on the investigator to thoroughly maintain the integrity of the image. Image integrity can be maintained using hashing methods.
Hashing can be performed using software utilities or mobile forensic software such as SPF Pro creates hashes from the initial acquisition steps.
Image hashing depends on the algorithm investigator defines to check data for integrity. The hashing algorithms such as MD5, SHA1, SHA256 are utilized to create a unique hash value. The hash value can be revalidated at any point in the investigation to denote that the image data stays intact.
Manual Hashing Methods:
While performing acquisition using the DD command, we can also hash the output image to file. Rooted Android device supports only the MD5 algorithm hashing by default.
Syntax:[dd if=/dev/block/memory-block /of=/sdcard/output-image.dd | md5sum > hash.txt]
Creates a DD image of the memory block and creates a text file with the computed image hash.
Hashing Using Software Utilities:
Forensic Software utilities provide the functionality to create hashes based on algorithms such as md5, sha1, sha256, etc.
Once we have generated a backup file of the Android device, the backup file is in .ab format and can be imported into a preferred analysis tool to parse the data and present it in a readable format, such as SalvationDATA’s mobile forensic system SPF Pro (SmartPhone Forensic System Professional).
SPF Pro supports to load and directly analyze an ab format ADB backup file, extract and present the acquired data in a way that is easy to read for forensic inspections.
Conclusion
Above is the forensic extraction procedure when we accomplished the complete extraction of digital evidence from Android devices using ADB commands. Android Forensic Investigation requires an investigator to be proficient regarding the extraction and analysis of evidence. The methods involved and the amount of data collected while performing device acquisition can become a crucial pointer determining the extraction of artifacts leading towards discovering evidence.

Android is a rapidly evolving operating system, hence the methods and acquisition methods will keep changing based on device & data access it is providing. Google timely releases patches for security enhancement and authorized device access. The extraction methods are also affected by the custom ROMs being developed by individual device manufacturers which causes an investigator to customize extraction methods every time. Thanks for reading!


