Editor’s notes: This February our SalvationDATA posted an article introducing the forensic technics to extract WhatsApp data from various kinds of situations. And in March, we released a free WhatsApp forensic tool which is capable of decrypting encrypted WhatsApp database files. If you missed our updates, don’t worry, check out the links below:

This news and updates have caught a great number of attention from our customers. It seems WhatsApp has always been a hot topic in the DFIR community. So today, after the release of our latest mobile forensic product SmartPhone Forensic System Professional (SPF Pro), we SalvationDATA would like to discuss WhatsApp forensics again and show you how to extract data from encrypted WhatsApp database files with the help of SPF Pro.
Extract and decrypt WhatsApp database backup
Step 1. Connect your smartphone to the PC with USB debugging enabled.

Step 2. Start the WhatsApp forensic tool, it can be found in SPF Pro’s toolbox. Select the target smartphone from the device list.
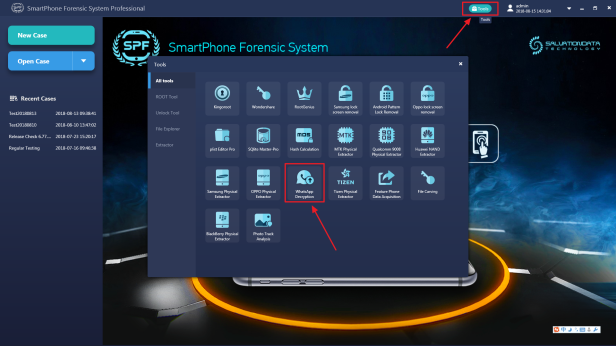
Step 3. Set your destination path for backup file storage.
Step 4 (optional). Load your encrypted backup. P.S. this step is optional, only load back up when you already have encrypted WhatsApp database files at hand.

Step 5. Press Start and follow the instructions to proceed. Be extremely cautious,
- The tool will first delete the current WhatsApp application, make sure to press No if smartphone notifies you to clear residuals.
- Then the tool will install an old version WhatsApp, make sure to allow installation if a notification pops up.
- After downgrade successful, the tool will create and extract backup, press “Backup my data” to allow backup.

Step 6. After the backup is complete, wait for the tool to restore the original WhatsApp application and finish the process.

Load and analyze the extracted backup
Step 1. Run SPF Pro or any other smartphone forensic tools you have that are capable of forensically extract and analyze data from smartphone database files.
Step 2. Create a new case or load a history case.
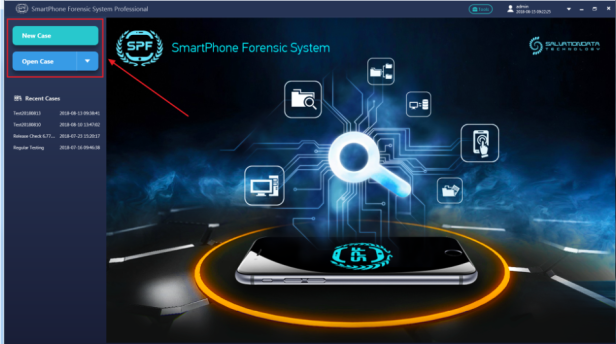
Step 3. In the device selection window, click ‘Folder Analysis’
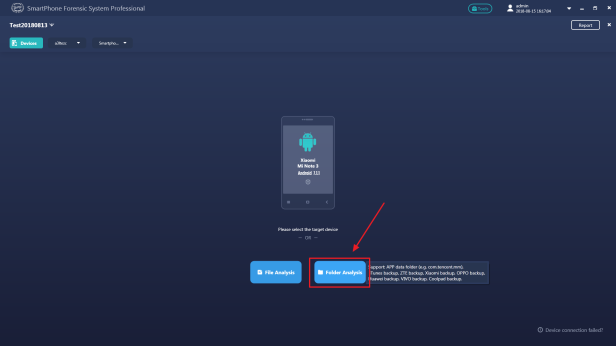
Step 4. Locate the decrypted WhatsApp files. And select it to analyze.
Please note: The ‘com.whatsapp’ folder must be in the 1st level or 2end level of the directory that you specified. In this case, we can select ‘DecryptedData’ or ‘com.whatsapp’ folder as extraction targets.

Step 5. Click ‘Automatic Logical Extraction’ or ‘Media File Extraction’.
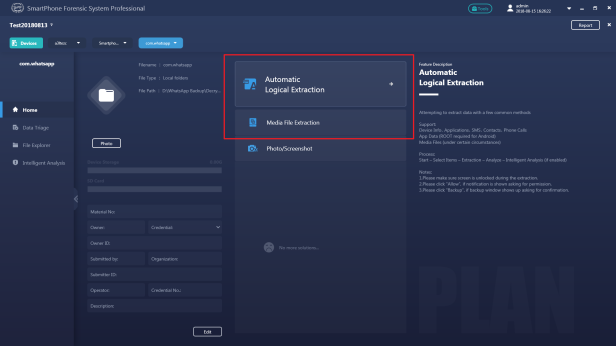
Step 5. Select WhatsApp for extraction, and click ‘Start Extraction’.
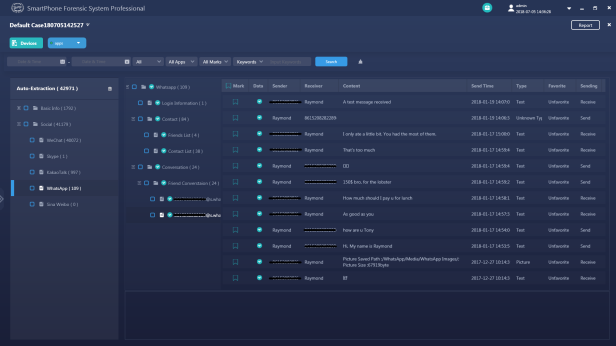
Conclusion
This article is an operation guidance on how to use SalvationDATA’s WhatsApp forensic tool and SPF Pro to decrypt WhatsApp encryption and how to extract unencrypted WhatsApp backup from unrooted smartphones.
You can find the motioned tools form our resources page. Our WhatsApp forensic tool is completely free to use. We welcome all our customers to download this tool, and hope it could help the DFIR community to solve more cases!
